how to send PRIVATE EMAILS
How to send private and encrypted emails in 2021 ?
Email is not private or secure.
It wasn’t designed with privacy or security in mind.
Anyone who handles your email in transit can read it,
including your ISP, a hacker, or the NSA (U.S. National Security Agency).
Summary:
- email privacy: what is happening today
- on the “legal” side
- on the “illegal” side
- email privacy: the challenges
- Anonymity and Confidentiality
- End-to-End Encryption
- email privacy: the solutions
- < technical > Pretty Good Privacy - also known as PGP
- < technical > How to use PGP encryption
- < easy > Alternatives to PGP encryption
what is happening today
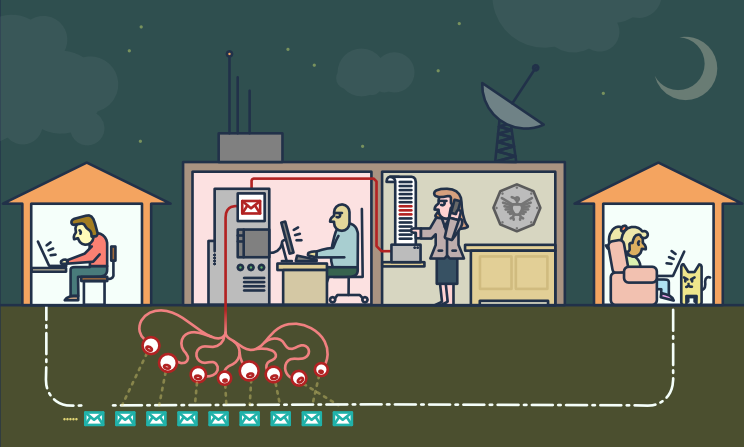
on the “legal” side
“The value of any piece of information is only known when you can connect it
with something else that arrives at a future point in time.
Since you can’t connect dots you don’t have, it drives us into a mode of,
we fundamentally try to collect everything and hang on to it forever.”
- - CIA’s Gus Hunt On Big Data, on The Huffington Post
- - CIA’s Gus Hunt On Big Data, on Youtube
“They’ve said it’s just metadata, it’s just metadata, […]
who you’re talking to, when you’re talking to them, where you traveled.
These are all metadata events.
PRISM is about content. […] They can all see it because it’s unencrypted.”
- - Edward Snowden - TED 2014
There are dozens of psychological studies that prove
that when somebody knows that they might be watched,
the behavior they engage in is vastly more conformist and compliant.
[…] mass surveillance creates a prison in the mind […]
- - Glenn Greenwald - TEDGlobal 2014
on the “illegal” side
Scammers might also use malware to infiltrate a company’s computer network
and access email exchanges about financial matters.
- - Fraud Resource Center - Business Email Compromise
Business email compromise (BEC)—also known as email account compromise (EAC)
is one of the most financially damaging online crimes.
In a BEC scam, criminals send an email message that appears to come from a known source
making a legitimate request […]
- - Scams and Safety - Business Email Compromise
the challenges
Anonymity and Confidentiality
Anonymity is different from confidentiality
[…] we’re encrypting messages
so that even if people see that we’ve sent a message
they can’t read what it is
but sometimes we don’t even want people to see that we sent a message at all
- - How TOR Works - Computerphile
Internet anonymity is difficult to achieve.
It requires a deep knowledge of the tools you decide to use.
This guide might give you an idea of its complexity:
Private Email Providers
Confidentiality is easier to get.
Even if you have nothing to hide, using encryption
helps protect the privacy of people you communicate with
and makes life difficult for bulk surveillance systems.
If you do have something important to hide, you’re in good company;
these are the same tools that whistleblowers use to protect their identities
while shining light on human rights abuses, corruption and other crimes.
The essential first step is to protect yourself
and make surveillance of your communication as difficult as possible.
- - Email Self-Defense - a guide to fighting surveillance with GnuPG encryption
End-to-End Encryption
End-to-end (e2ee) encryption for email can be used to ensure
that only the sender and the recipients of a message can read the contents.
Without this protection it is easy for network administrators,
email providers and government agencies to read your messages.
Achieving e2ee requires carefulness by both the sender and the recipients.
A single mistake by any of the involved parties can be sufficient to break the security of e2ee.
Email metadata, such as sender email, recipient email, date and time, cannot be protected using e2ee.
The subject of the mail may also remain unprotected and easily readable, even when e2ee is used.
- - What is End-to-End Encryption in Thunderbird?
the solutions
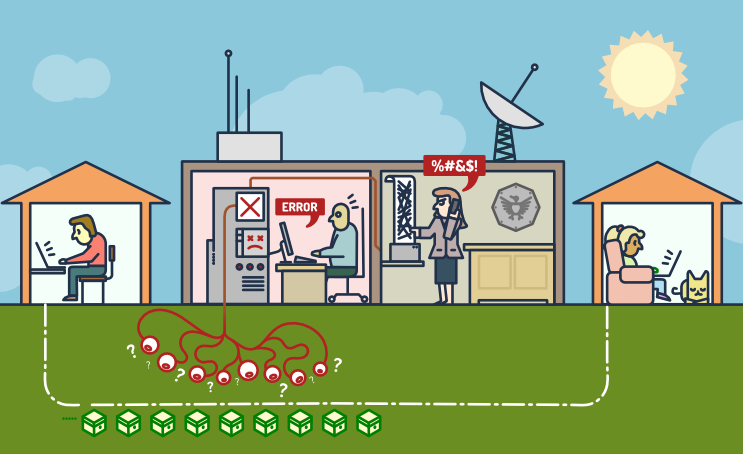
< technical > Pretty Good Privacy - also known as PGP
PGP software follows the OpenPGP standard of encryption,
standard (RFC 4880) for encrypting and decrypting data.
- - Pretty Good Privacy on Wikipedia
PGP encrypts your email body into a code
that only the right person can read.
PGP runs on pretty much any computer or smartphone.
It’s freely licensed and costs no money.
Each user has a unique public key and private key,
which are random strings of numbers.
Your public key isn’t like a physical key, because it’s in an online directory, where people can download it.
People use your public key, along with PGP, to encrypt emails they send to you.
Your private key is more like a physical key, because you keep it to yourself (on your computer).
You use PGP and your private key to decode encrypted emails other people send to you.
If an email encrypted with PGP falls into the wrong hands, it’ll just look like nonsense.
Without the real recipient’s private key, it’s almost impossible to read it.
To protect ourselves form surveillance, we need to learn when to use PGP
and start sharing our public keys whenever we share email addresses.
- - Email Self-Defense - Infographics
< technical > How to use PGP encryption
To use PGP, you’ll need a public key and a private key (known together as a keypair).
Each is a long string of randomly generated numbers and letters that are unique to you.
Your public and private keys are linked together by a special mathematical function.
An application that manages the keys and the encryption/decryption of messages is required,
this is a selection of the most popular ones:
Mailvelope is a free, open source, browser-plugin, available for Mozilla Firefox and Google Chrome,
it’s probably the easiest way to approach PGP
“Mailvelope Demonstration” is a well done tutorialMozilla Thunderbird application integrates everything needed to send PGP signed messages
Introduction to End-to-end encryption in ThunderbirdGnuPG is a complete and free implementation of the OpenPGP standard
A Noobs PGP Guide using Gpg4Win [Easy 5 Min Setup] explains how to use it
< easy > Alternatives to PGP encryption
PGP is the best solution for secure communications with a partner that is already using it.
Asking your counterpart to start using PGP could be hard.
The services that allow you to share a secret only once are an alternative.
When sending something a single time, there are open-source web apps
that allows you to enter information that can only be viewed once.
After the recipient has opened the page, the information is deleted,
and the only thing remaining in your chat logs or email is a bad link.
It’s not as robust as your entire team using PGP, but it’s much easier to set up or explain.
We’ve been able to use it to send login information to fairly non-technical people, and they find it easy to use.
Example (without adding a password):
Let's say you have a password. You want to give it to your coworker, Jane.
You could email it to her, but then it's in her email, which might be backed up,
and probably is in some storage device controlled by the NSA.
If Jane gets a link to the password and never looks at it, the password goes away.
If the NSA gets a hold of the link, and they look at the password... well they have the password.
Also, Jane can't get the password, but now Jane knows that not only is someone looking in her email,
they are clicking on links.
Some of these services, all free and opensource, are listed below.
You could also decide to host an instance on your own webserver.
PrivateBin (like a secure version of PasteBin) is developed in PHP
PrivateBin code is published on Github - 3100 stars
PrivateBin instructions are available on a different website
OneTimeSecret is developed in Ruby
OneTimeSecret code and instructions are published on Github - 1200 stars
SnapPass is written in Python. It was originally developed by Pinterest
SnapPass code and instructions are published on Github - 600 stars